Article Top 5 essential tips for hardening your security posture in Microsoft 365
Top 5 essential tips for hardening your security posture in Microsoft 365
In the modern digital landscape, where cloud-based productivity tools like Microsoft 365 have become more widely adopted, it has never been more important to secure your organisation's data and apps with diligent and proactive measures to enhance and harden your cyber security posture.
By Insight UK / 1 Jun 2023 / Topics: Cybersecurity
In collaboration with: 
In this blog post, we explore the top five steps you need to take to bolster your security in Microsoft 365 and safeguard your sensitive information from cyber threats.
1. Enable Multi-Factor Authentication (MFA)
This one may seem all too obvious, but it’s truly alarming just how many organisations still have not done this. MFA is THE fundamental step in securing your Microsoft 365 environment. It requires your users to provide an additional layer of authentication along with their passwords, to ensure that even if passwords are compromised, unauthorised access by malicious actors is significantly more difficult to achieve.
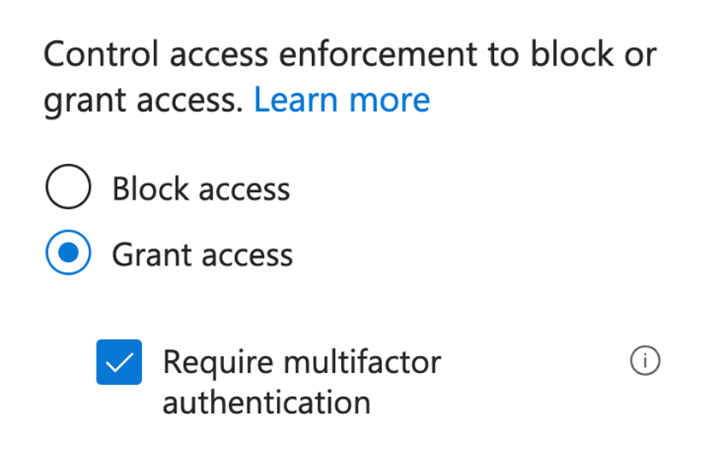
Figure 1: Enforcing MFA with Azure AD Conditional Access
There are various methods available to implement MFA in Microsoft 365, including Security Defaults and Azure AD Conditional Access, and there are several authentication options such as text message codes, app codes and notifications, number matching, biometric scans, and hardware tokens. Enabling MFA for all user accounts in your organisation should be your top priority, and Conditional Access is the best and most effective way to implement MFA.
2. Implement Conditional Access Policies
MFA is the most basic example of what Azure AD Conditional Access does, but it is also so much more. With Conditional Access, you can define access rules based on specific conditions that ensure controls are in place to allow only trusted devices and users appropriate permissions to access your organisation's data. Some examples of common Conditional Access policies are shown in Figure 2.
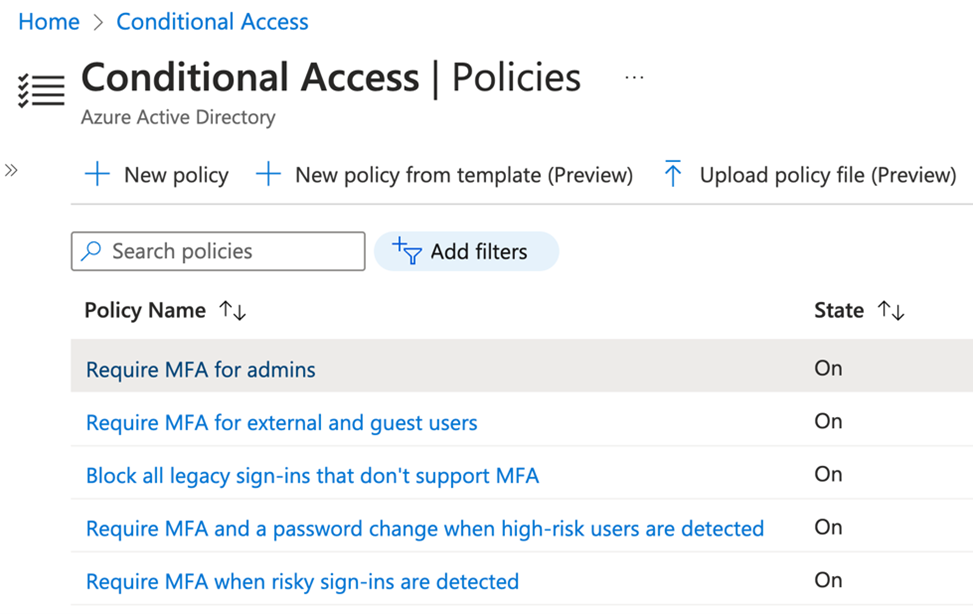
Figure 2: Example Conditional Access Policies
Conditional Access is a powerful way to ensure that users can securely access your Apps and Data on Microsoft 365 only from the devices and apps that you choose, and from specified locations. As an example, you could create a policy that requires users to access their email on their devices only from an approved app such as Microsoft Outlook.
3. Use Privileged Identity Management (PIM) to manage privileged roles
There are many roles within Microsoft 365 and Azure that have powerful privileges, and which can have very dangerous consequences in the wrong hands. Roles such as global administrators should be kept to an absolute minimum, and wherever possible, privileged admin roles should not be permanently assigned to your users.
PIM allows your organisation to reduce the risk of your privileged admin roles becoming compromised by making users eligible to activate the roles only for short periods of time when they need elevated access on a just-in-time basis.
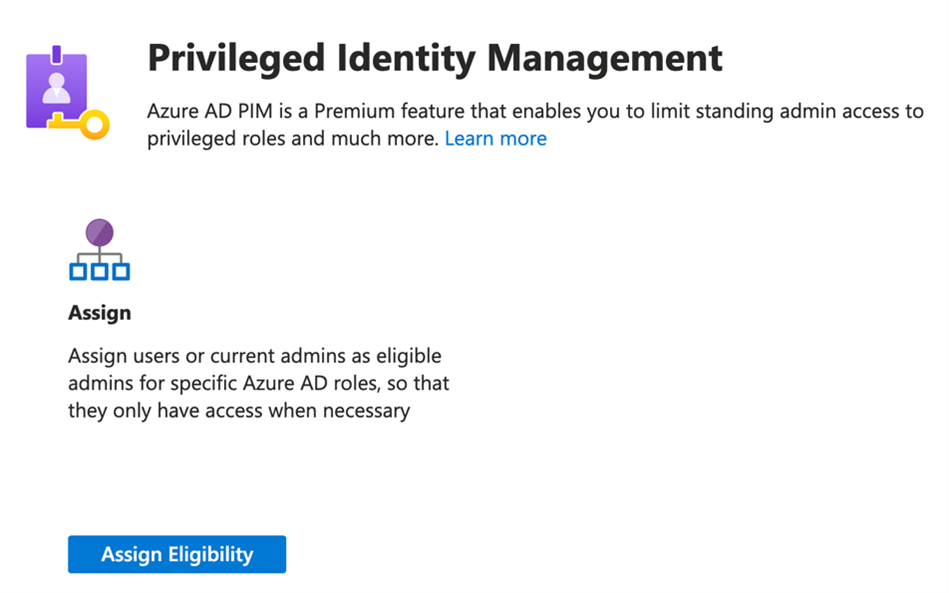
Figure 3: Assigning eligibility to users for privileged roles
If you have Azure AD Premium P2 licencing in your Microsoft 365 environment, PIM is a feature that can help you to reduce your attack surface, and one which you simply cannot afford to ignore. Take the time to understand the privileged roles available in Microsoft 365, and consider who needs access, and how frequently. Then, assess any standing access your users have to privileged admin roles. You will probably be surprised how over permissioned many of your Microsoft 365 user accounts are, and this is a significant risk to your organisation.
4. User education and awareness is key
The importance of the human factor in relation to cyber security cannot be underestimated, and it is absolutely crucial to promote user awareness throughout your organisation.
Educate your users about common threats such as phishing attacks, social engineering, and malicious email attachments. Encourage them to use strong, unique passwords, avoid sharing sensitive information, and report any suspicious activities promptly.
With Microsoft 365 E5, you can also configure Attack Simulation Training for your users to help them to be better prepared for many different types of attacks.
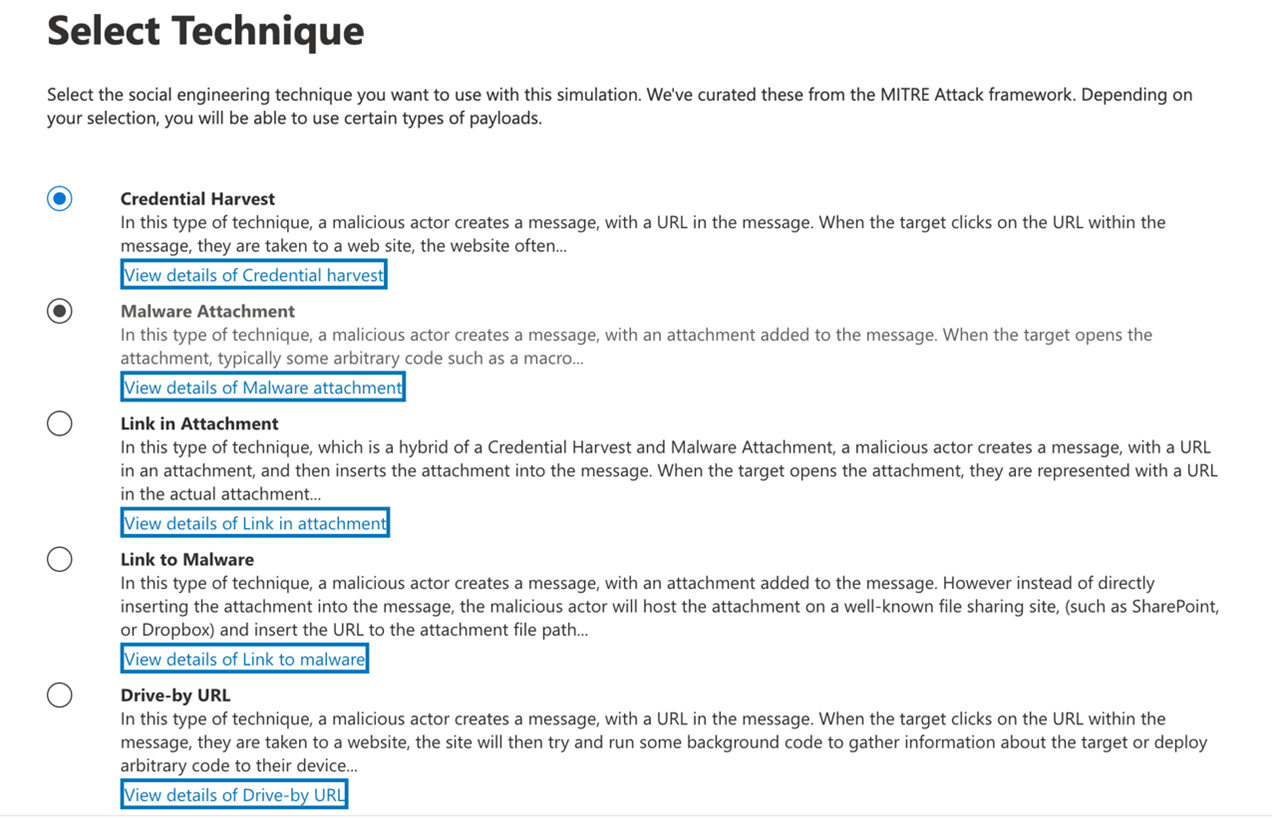
Figure 4: Attack Simulation training in Microsoft 365
Plan to conduct regular security awareness training sessions to keep your users informed about the latest security trends, best practices, and the importance of maintaining a security-first mindset.
5. Understand that your Data is your most precious asset
All too often, organisations will focus on protecting their Apps and Devices. However, Data is the lifeblood of any organisation, and it is your data that malicious actors are focused on when they launch an attack. Data is like gold to an attacker. They can sell it, ransom it, and once they have access to it, your organisation is at risk of loss of productivity and reputational damage.
With Microsoft Purview, you can put effective measures into place to protect, govern, and keep your data private.
An effective Data Classification strategy is crucial for your organisation and will help you to:
✓ Know your Data
✓ Protect your Data
✓ Prevent Data Loss
✓ Govern your Data
These principles are illustrated in Figure 5.
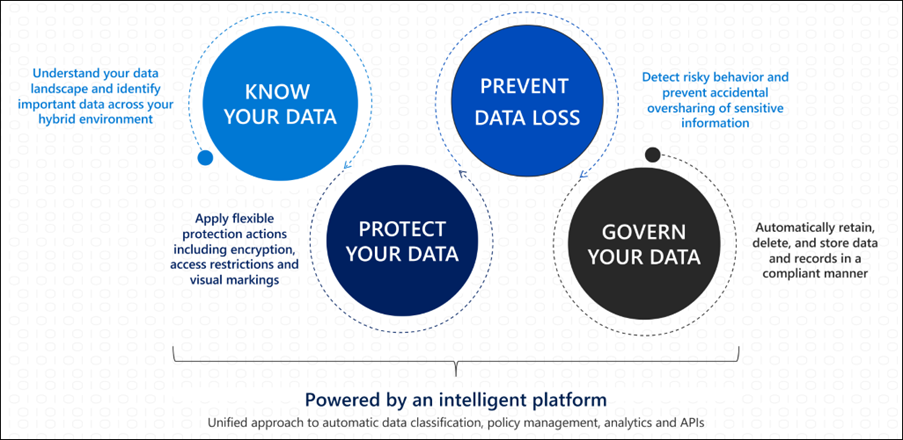
Figure 5: Data Classification Microsoft 365
With Microsoft Purview, you can deploy tools like Sensitivity and Retention labels, Data Loss Prevention policies, Privacy and Insider Risk Management, and more to provide your organisation with a robust data protection posture that can prevent data breaches and loss, and will save you time, money, and damage to your reputation.
Summary
These are just a few tips that can help you to safeguard your data, apps, and devices with Microsoft 365. There are many other approaches to enhancing your security posture, and Insights Microsoft Certified Architects and Consultants can help you roadmap a cyber security strategy appropriate to you, in an ongoing process to adapt and evolve your security measures and address emerging threats in the ever-changing digital landscape.
Want to learn more? Register for our Security Workshop on Top 5 essential tips for hardening your security posture in Microsoft 365.
Peter Rising
Consulting Manager: Security & Compliance
Peter Rising has over 25 years’ experience in IT. He has worked for several IT solutions providers and private organisations in a variety of technical and leadership roles focusing on Microsoft technologies. Since 2014, Peter has specialised in the Microsoft 365 platform, more recently shifting his focus to Microsoft 365 Security and Compliance. He holds a number of Microsoft certifications, and has twice been recognised as a Microsoft MVP for contributions to the technical community.
Peter has authored several books on Microsoft administration and study guides, and has two YouTube Channels where he shares his passion for community, and technology.




